A certified ethical hacker is a talented professional who knows and understands how to observe vulnerabilities and weaknesses in target systems and utilises these tools and knowledge as a malicious hacker, but in a legitimate and lawful manner to study the security posture of target systems. The credential of CEH certifies individuals in the particular network security area of ethical hacking from the perspective of neutral-vendor.

The use of CEH credential is to:
- Govern and establish least standards for providing the credentials to professional information security specialists in the measures of ethical hacking
- Notify the public that individuals which are credentialed exceed or meet the least standards
- Strengthen ethical hacking as a self-regulating and unique profession
The training program of certified ethical hacker is the highest point of most desired training program related to information security any information security professional want to be a part of. This course provides the modern hacking techniques and tools used by information security professionals and hackers in the same way to hack an organization. This training will enable you think like a hacker so that you can prevent attacks in the future. In any organization, the security mindset should not be limited to silos of pieces of equipment, technologies or the silos of a particular vendor.
The ethical hacking training enables you to be in a driver’s seat of a hands-on environment of a methodical process. Here, you will learn how to attain posture pertaining to optimal information security in their company through hacking. You will secure, hack, test and scan your systems. You will come to know the five aspects of ethical hacking and the means to reach your goal and be successful in the hacking process every time. The five aspects include covering your tracks, maintaining access, reconnaissance, gaining access and enumeration.
We live in a world where unauthorized access to information can be from any place and at any time and we are never aware how persistent, skilled or well-funded the threat will be. Throughout this program, you will be submerged in the mindset of a hacker, evaluating the security physically and logically. Searching every possible entry point to gain the weakest link in a company from the perspective of end user, CEO, security, vulnerable times during migrations, data left in the dumpster, and misconfigurations.
Ethical hackers require on-the-job training to get expertise in it and have a career in it. Major IT giants like IBM and other type of organizations are employing a team of ethical hackers to maintain security for their systems. Today, hiring of ethical hackers has become compulsory for almost all the organizations.
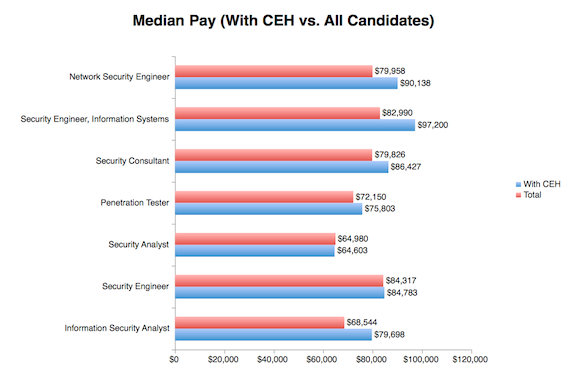
Source Image: payscale.com
The Bureau of Labor Statistics is expecting the IT security field to grow upto 37 percent by the end of 2022 and according to Ponemon Institute’s survey, almost 30 percent of the IT security jobs are vacant and demand for IT security professionals is very high. The pay is also extremely good for certified ethical hackers. The average salary for an information security analyst in US is $90,000 a year and if he/she has experience and good hacking skills can earn upto $100,000 a year. If you are ready to wear your “white hat” and invade the systems for a good cause, this job role can be an excellent career opportunity. So, people looking for this career can receive training in certified ethical hacker and become expert in it.

Jimmy is a dedicated and experienced author of this tech blog. He wants to be helpful and offer great content to his readers, but he also needs to make sure that the site is profitable so it can continue running. If you have any questions or concerns about our work please don’t hesitate to contact us!