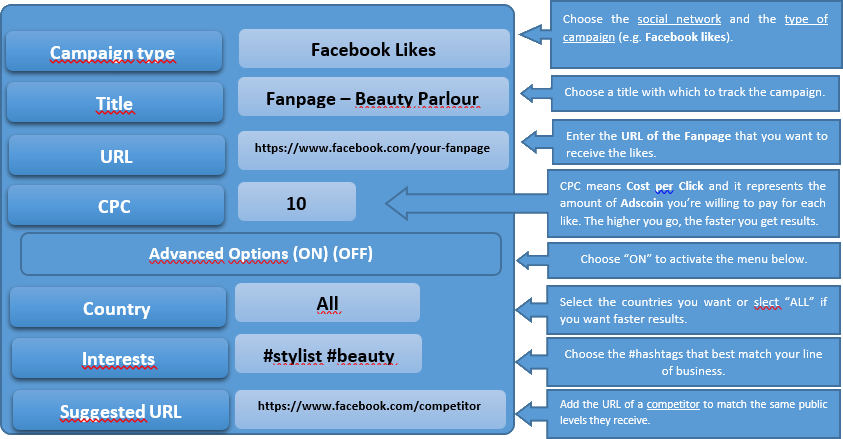
STRIDE Threat Modeling is a process that can be used to identify security risks in systems and software. The acronym STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. This methodology is a useful tool for security analysts and developers to identify potential security risks during the design phase of a system or application.

The STRIDE methodology is based on the concepts of attacks and countermeasures. An attacker will use one or more attack vectors to exploit system vulnerabilities to achieve their goals. A countermeasure is a security measure that is implemented to mitigate or eliminate the risk of an attack. The STRIDE methodology can be used to identify security risks in any type of system. However, it is especially useful for identifying risks in web-based applications. This is because web-based applications are typically more complex than other systems and are often more susceptible to attack.
When using the STRIDE methodology, analysts and developers will first identify the most important assets to protect. They will then identify the threats that could potentially exploit vulnerabilities in those assets. Finally, they will identify countermeasures that can be implemented to mitigate or eliminate those risks.
The STRIDE threat modeling example is a useful tool for security analysts and developers to identify potential security risks during the design phase of a system or application. This methodology can be used to identify security risks in any type of system. However, it is especially useful for identifying risks in web-based applications.
Organizations that use STRIDE can benefit from reduced security risks and improved customer confidence. STRIDE can also help organizations to meet compliance requirements, such as those set by the Payment Card Industry Data Security Standard (PCI DSS).
STRIDE is just one of many tools that can be used to assess security risks. When used in conjunction with other tools, STRIDE can provide a comprehensive view of an organization’s security posture.
See Also: Top 4 Benefits of Using a Pick Up and Delivery Courier Service

I’m Kelly Hood! I blog about tech, how to use it, and what you should know. I love spending time with my family and sharing stories of the day with them.